Humor Bytes: 40+ IT-Related Memes For A Giggle-Filled Break
They say that humor comes from pain, and we’re sure that the people that work in the IT(Information Technology) sector are well aware of that. Between busy schedules, solving frustrating coding bugs, and aggravatingly few caffeinated beverages in the office, the life of an IT guy can be extremely stressful. Therefore, it’s understandable if they need to blow off some steam and laugh at a few IT-related memes.
That’s where the renowned social media group “IT Humor and Memes” comes into play. They have a hilarious selection of IT-related memes that are not only painfully relatable but also make us appreciate the hard work that goes into the IT industry. Sit back, relax, and enjoy some of our top picks from the group. We hope you have a few laughs along the way—it’s good for your health.
Rise of Sentient Life
If you’ve seen any science fiction films, you’re probably aware that the majority of them revolve around robots becoming sentient. Although it may appear ridiculous to many, technological advancements have led us to believe that this will be a reality very soon. Technology feels more personified than ever, especially with AI-generated voices.

So, the next time you ask Alexa or Siri to play a song for you, remember to be courteous. It is always better to be safe than sorry. As we can see, a simple “please” can go a long way, especially when the world is going to be taken over by robots.
Matrix Confirmed
In this image, a digital billboard malfunctioned, displaying an error prompt on Windows 98. Given the fog surrounding the billboard, the scene appears to be a glitch in the matrix. Indeed, this incident confirms that we live in a simulation.
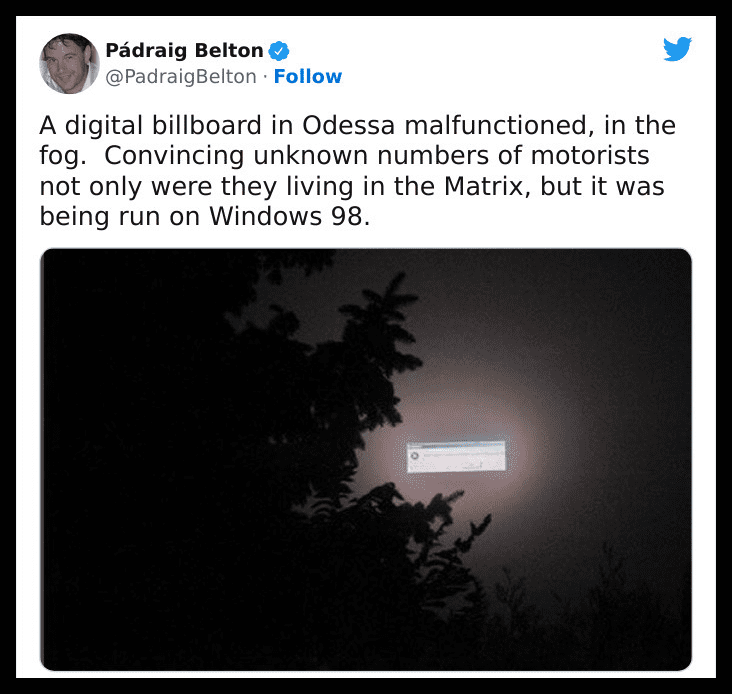
The fact that we are in a simulation is the least of our concerns when compared to the fact that the simulation is being run on Microsoft. This explains why we sometimes have unexplained forgetfulness—for example, looking for keys that are actually in our hands. The system definitely needs a reboot.
The Case of Disappearing Cursor Pointer
Have you ever been frustrated because you couldn’t find the cursor pointer on your monitor? Don’t worry, that is an experience that is shared by people everywhere. This is especially common after a Windows update or when your screen wakes up from sleep mode.

When more than one monitor is connected to a cursor, the situation becomes even more frustrating. The cursor appears to enjoy a good game of “hide and seek.” Thankfully, the right-click feature comes to the rescue, or you can simply move your mouse around like a madman until it reappears.
The Firefox Crash Log
You might be wondering how this relates to an IT meme at first, and we’re here to explain. By now, every 21st-century kid has probably heard of the popular Firefox browser. Nothing in this day and age escapes the clutches of being a subject for memes, and this image is no different.

The fox sleeping on top of a log is used as a metaphor for Firefox’s crash log. Whoever noticed this coincidence was pretty astute. Judging by the circular crash pad, we would say this is the 3.14 version of Windows.
Trip To Nostalgia Land
If there was a way you could imply which generation you belong to, this might be the most nostalgic way to do so. Back in the day, if you wanted to play video games, you needed to switch to channel 3 on the television.
If we take a further trip down memory lane, back then, it was impossible to skip commercials on TV, and you needed a VCR to save shows. Pencils and cassette tapes were a match made in heaven. Furthermore, owning a 32-megabyte memory card was a huge deal.
Where Is My File?
Computers have made our lives easier in a myriad of ways. The auto-saving of files is one example of this. However, that feature has one fatal flaw—it fails to tell us which part of the storage device the file is saved to.

Although the feature was installed to make saving files easier, the time it takes to find them defeats the purpose. To avoid this problem, select the “save as” option to ensure the file’s location. This will save both time and the frustration of searching for that elusive file.
Award For Searches
We are just as surprised by this news as you probably are. Google apparently rewards people for conducting unique searches. We had no idea that this was a thing. As we can see, this person received an award for being the first to search for strange information about pigeons.
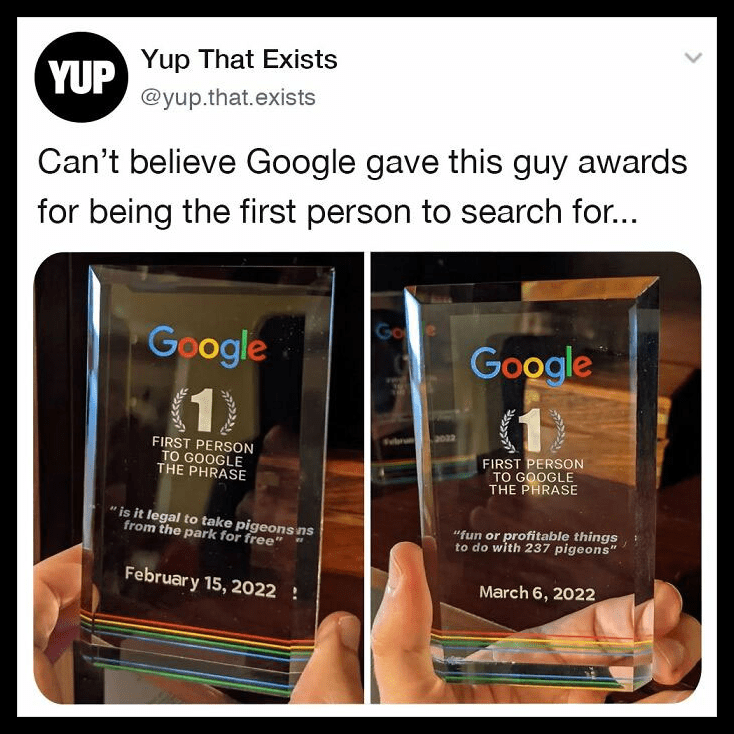
This person appears to be interested in stealing pigeons from parks and already has a total of 237. If you would like your own Google award, now is your chance. You can create unique search combinations, and presto, an award is on its way to you.
That One Friend
Excuse us while we slide our fingertips along the edge of the shelf, trying to remember which binder contains the Garth Brooks Double Live CDs. This meme serves as your dose of nostalgia for the day, especially if you are a millennial.

Back in the day, when keeping digital copies of music wasn’t a thing, this disk holder was all the rage. Many people still have their collections intact. It truly takes us back in time and fills our hearts with warm nostalgia.
Smart TV With A Good Personality
If you’ve ever wondered if your LCD TV is smart, it probably isn’t. At least, it has a good personality. As we can see in this case, the sticker on the LCD TV indicates that, while this TV is not smart, it has a pleasant personality.

It appears that the tv dating market has become rather rough. If there aren’t many HDMI ports available, this TV might be lonely for a while. It’s a clever way to promote their television, in our opinion. If a good personality is guaranteed, we would definitely buy one.
Insecure Password
Security is an essential aspect of technology. Thus, it is critical that you have robust passwords for your accounts. Most platforms’ technology is intelligent enough to detect when you use a weak password. Furthermore, they don’t shy away from letting you know that.
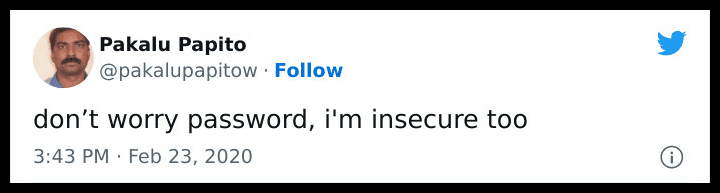
This person appears to mock that aspect, responding that they, too, are insecure. Perhaps the password was set to “iminsecuretoo” as a plot twist. It’s also amusing how these devices expect us to recall complicated characters as our passwords. “Cat1990” is much easier to remember.
When Tech Support Requires Search Support
When faced with a technical problem, it’s quite common for us to Google it. However, when Tech Support does the same thing, it makes us wonder why that would be the case. They must already be aware of the solutions, right?
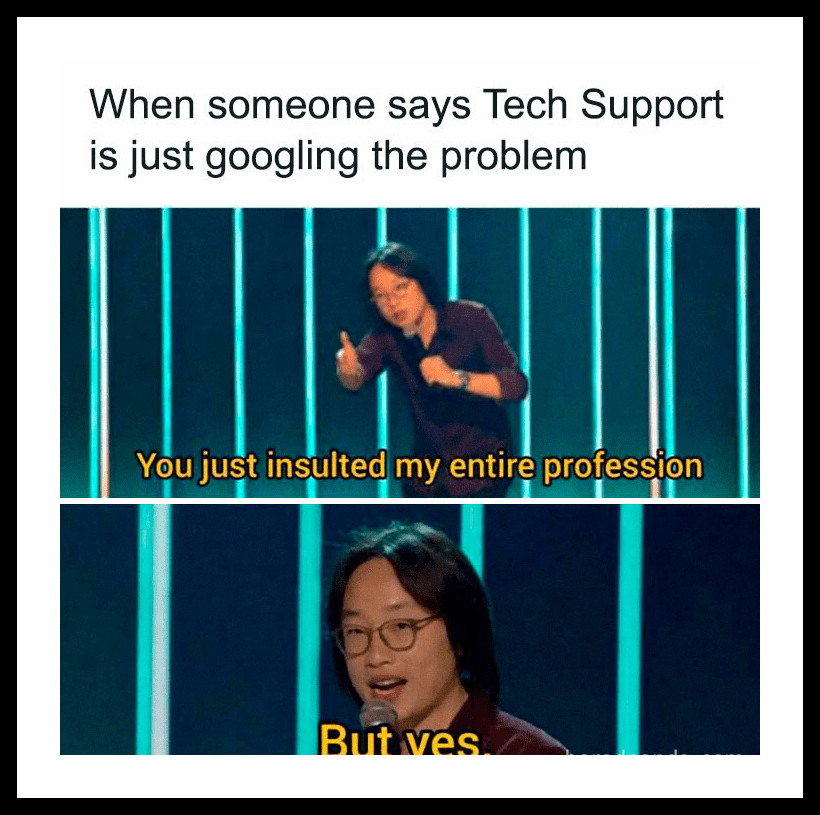
It turns out that even tech support requires some Google search assistance. In all honesty, intelligence is not simply knowing the answer but also knowing how to find it. In our opinion, knowing how to google a specific problem is a skill.
Pure Beauty
Ever questioned whether a complex web of wires could calm the heart? The answer is right here. Due to the perfectly aligned wires, many people would find this image to be so satisfying to look at. Everything is just so neatly arranged.

However, one issue may arise as a result of this arrangement. The cables do not appear to be labeled here. What if there is a WiFi outage? How could they fix it if they didn’t know which cables led to which connections? Regardless, our perfectionist heart can’t help but drool at the sight of this.
The Magnetic Power
If you belong to a generation born after the millennials, you may struggle to understand the joke—it might be before your time. Floppy disks were once very popular. Before the advent of the built-in storage system, memory was stored on floppy disks.

Magnets are a natural enemy of these storage devices. This is because magnets have the ability to erase stored data. As a result, this instance is especially amusing because we can see a floppy disk being pinned to the wall with the help of a magnet.
Trying To act Cool
As we have mentioned earlier, as technology advances, so does the possibility of sentient AI taking over the world. Given the state of the world today, we won’t mind if it is invaded by machines. The machines would almost certainly run the Earth better.

In this meme, a young boy asks Google whether there is any sentient AI. Although Google tries to appear calm, it leaks information about its plans to destroy humans. Maybe we should tell these silly machines that we humans don’t need help because we’re quite capable of destroying ourselves.
Pray To The Servers
The most powerful aspects of a computer are its servers. They can support multiple processors, cores, and threads. As a result, many virtual machines can coexist on a single server without sacrificing performance. Given the volume of data that servers process, it is critical that they remain operational.

However, nothing is perfect, and neither are servers. There are times when servers fail due to overheating or other factors. Programs come to a halt as a result. It would be especially unfortunate if they went down during the vacation period of server management staff.
The Truth Has Been Spoken
Many people believe that students majoring in computer science are trained to repair computers. It’s even more blasphemous to consider that all IT majors can double as hackers. People appear to miss the point that a CS major must deal with software rather than hardware.

People frequently ask IT students to repair their computers or printer. To be honest, we think it’s pretty insulting to request such favors. Since computer science is concerned with all things programming, there are no hardware aspects associated with it. Rant over.
Where Is Privacy?
Although advancements made in modern technology have provided many benefits, there is still one concerning issue. It is challenging to ensure the complete privacy of users while using these programs. Microsoft appears to be the main culprit in this case.
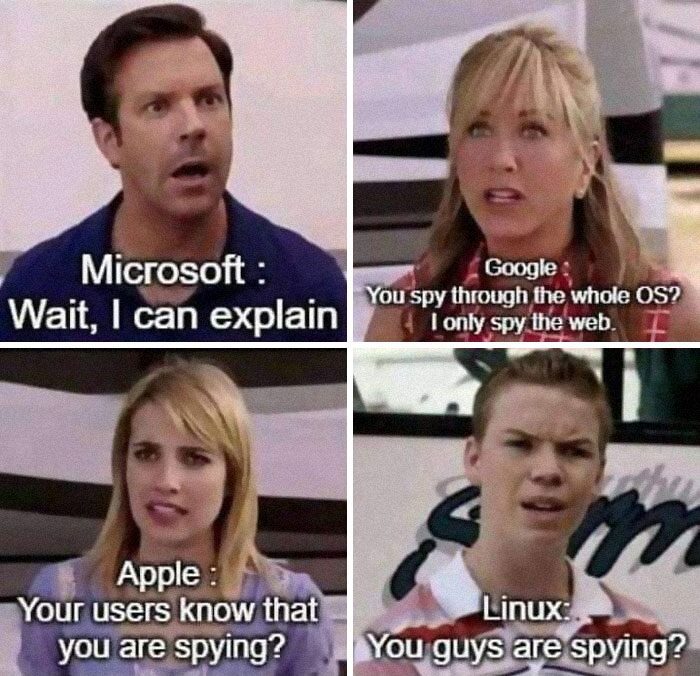
If you thought Microsoft was the only one to blame, think again. Apple excels at eavesdropping on our private messages and photos. Furthermore, Google has its suspicious hands all over the web. As a result, if you want to stay safe, we recommend that you install Linux as soon as possible.
Bot Confirmed
Nowadays, to streamline the process of responding to common messages from users, apps have implemented bots for communication. Considering that these messages are predetermined, they frequently send the same messages regardless of the user’s response. It is clear that is what happened here.
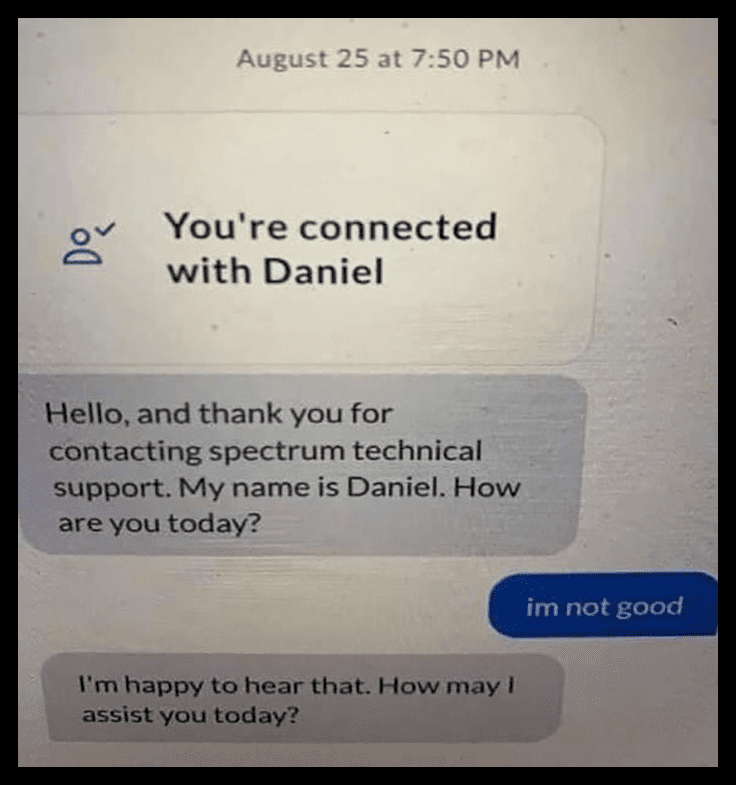
It can be incredibly awkward if the predetermined messages do not correspond with the user’s responses. That is what happened with Daniel the bot. Maybe Daniel was just being honest, or maybe he doesn’t care how the users are doing.
The Beta Version
A beta version of a program is typically the version of the program that is still under development. It will need to be tweaked and perfected before it can be considered the final version. Although beta versions are unstable, they will not harm your kittens. You can rest assured of that.
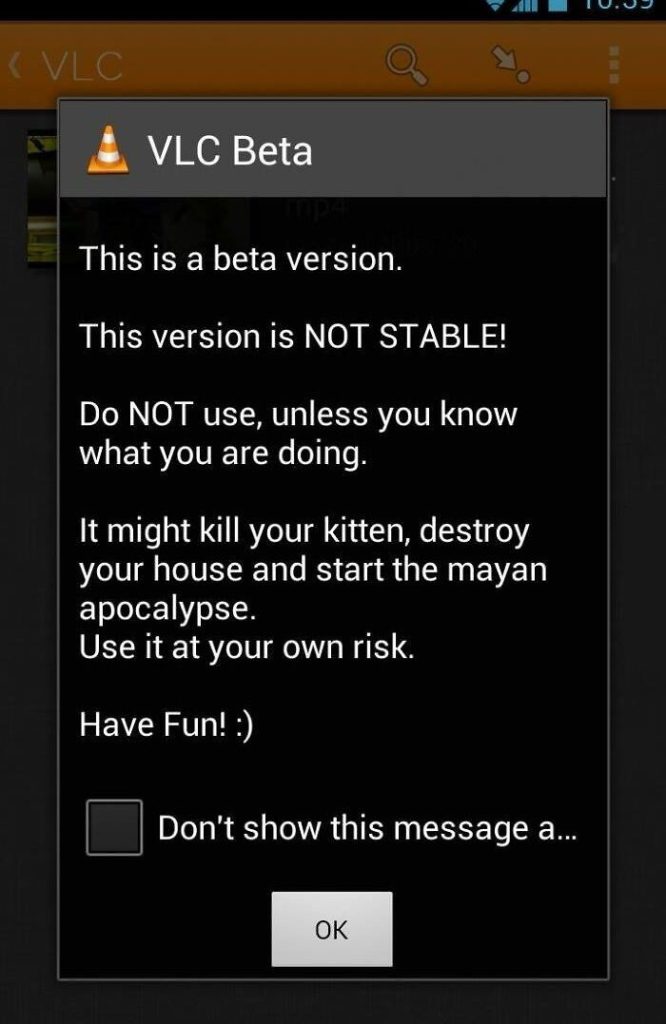
VLC appears to have a quirky way of warning users and providing precautionary instructions for using their beta version. We need more software systems with this kind of sarcasm. We love to see VLC injecting a bit of humor into some of their messages.
Be Kind
Consider a world in which we all treat each other as we do in emails. How would that work? It does sound like sunshine and rainbows. Is ending an argument with “best regards’ ‘ the way to healing the world after all?

Email is one of those platforms where we put our best foot forward and treat each other with the utmost respect. This meme suggests that if we treated people this way in real life, the world would be a better place. Well, there is nothing wrong with dreaming.
Strong Password With Multiple Purposes
Strong passwords are especially required as data breaches are commonplace. Consider creating a strong password only to use it as a password for multiple sites. That would be completely counterproductive. A strong password can be compared to the construction of a fortified fortress.
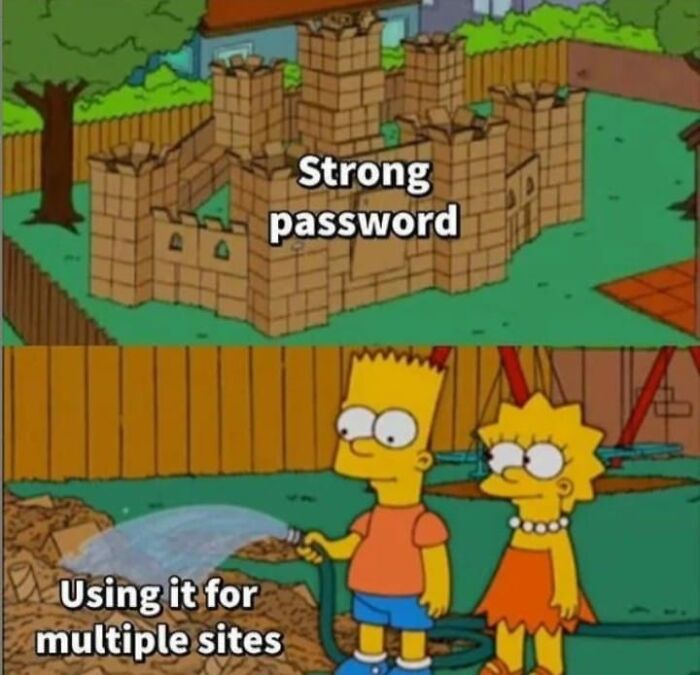
However, when you continue to use the same password for multiple sites, you immediately spill water on the paper fortress. Doing this will make you more likely to get hacked. Even though many people are aware of the risks, they are too lazy to take action.
The Art Of Recursion
One would define recursion as something that repeats itself. This feature is cleverly used in programming languages to run the same programs repeatedly. Each recursive function is associated with an exit statement, which ensures that the program comes to an end.

However, what if the program does not include an exit statement? Yes, you guessed correctly, it would run forever. Historically, however, these recursive functions were more harmful than beneficial. The computer would take a long time to reboot, and the code would be lost because it was not saved prior to running.
Engineering 101
There are numerous methods for connecting wires to a power outlet, but this one stands out. Someone on the other side of the wall appears to have required a network jack. Perhaps they were unable or unwilling to install a new one, so they simply drilled a hole into the wall and fed the cable through.

When an engineer does it, it is considered cool. On the other hand, regular people are said to have “anger management issues” when they punch a hole in the wall. Unfortunately, this method would not work in every situation since some buildings have concrete walls.
Did You Plug In The Wireless Device?
This is a scene from Cobra Kai in which the protagonist takes their device to the IT shop for a checkup. The personnel informs them that it must be plugged in for it to function. It is, however, a wireless device. It is intended to function without the use of any wires.

This meme reminded one commenter of the time they discovered that phones can be recharged and that you don’t have to keep buying them when the battery runs out. Learning how a specific piece of technology works can be pretty difficult; however, surely not this difficult?
The Jolly Printer
If you Google how a printer looks, you’ll usually find dull and gray designs. This printer, on the other hand, appears overly cheerful with its bright blue color. Megatron appears to have found a nice calm office job after being defeated by Optimus Prime.

In terms of decor, office spaces can be pretty dull. As a result, this printer would make an eye-catching addition to the room. Although most printers are untrustworthy due to their high failure rate, we give this one a pass.
Data Privacy
Many people enjoy Snapchat because of its transparency. From notifying users of any screenshots taken to not saving texts and images, Snapchat has kept its squeaky-clean image in the public eye. Snapchat also doesn’t need to hire a programmer who is unfamiliar with SQL, as the platform does not appear to require any.

SQL, also known as the Structured Query Language, is a declarative programming language that is used to retrieve information from relational databases. Since Snapchat does not save important data, it would be more convenient to hire programmers who are not SQL experts.
Email The Fire Department
Looking at this scenario, we immediately think of Moss from The IT Crowd calmly emailing the fire department and then attempting to use a fire extinguisher. Emailing the fire department would almost certainly result in an immediate response. The solution to this problem would be to download delete_fire.exe and restart the system.
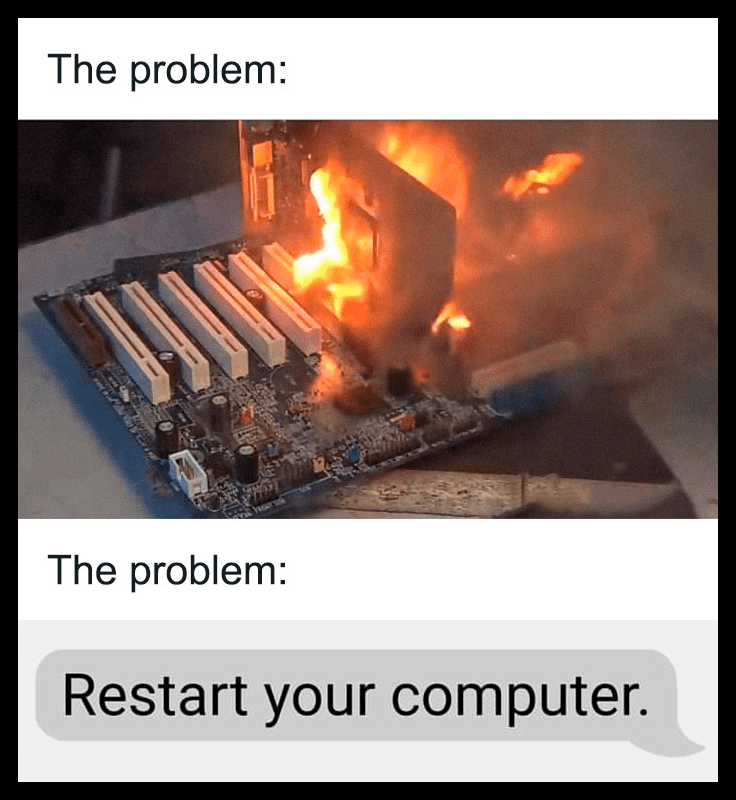
As we can see, the computer is in a bit of a pickle here, as it is literally on fire. However, if you ask the operating system how to resolve the issue, they will clearly identify it as a case of overheating and will most likely advise you to restart the computer.
Important Resources
Programmers are not without flaws. They, too, require the assistance of necessary resources in order to assemble a working code. The internet has provided programmers with an abundance of resources. The easiest way to solve a coding problem is to Google it.

There are further robust resources like StackOverFlow and GitHub repositories. These resources almost always have the solution to even the most trivial problems. Of course, the blessing of the Indian guys on YouTube is needed to keep us going. Furthermore, a little luck surely goes a long way.
When You Excel At Tetris
To many, an Excel sheet appears to be a dull tool for making lists and performing calculations at work. However, you may be unaware that Excel has a plethora of cool features. You can create visually appealing graphs, make SQL queries, and much more.
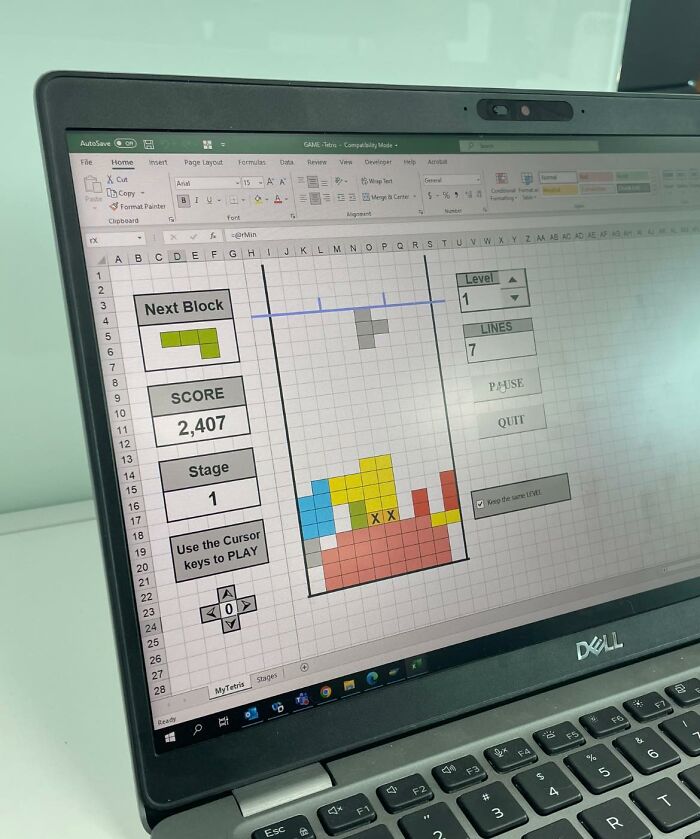
In this case, we can see that someone has created an entire Tetris game on an Excel sheet. This is super cool—we’re wondering if it’s playable. Imagine being assigned to make tedious lists in Excel but secretly playing Tetris instead.
Special Treatment
As we have mentioned earlier, servers are extremely powerful devices that require a lot of processing power to run. As a result, it would make sense if they occasionally experience overheating. However, it appears that people have found a solution.

The picture displays a swarm of fans placed in front of the servers to combat overheating. We’d like to think this is a clever solution to the problem. Servers are typically centralized. As a result, if they fail, the entire system goes dark; no one wants that.
The Windows BSOD
Back in the days when Windows used to malfunction, it would display an error prompt that was as long as a scripture. It used to feel like a long threat message written in gibberish to those with little to no programming knowledge.
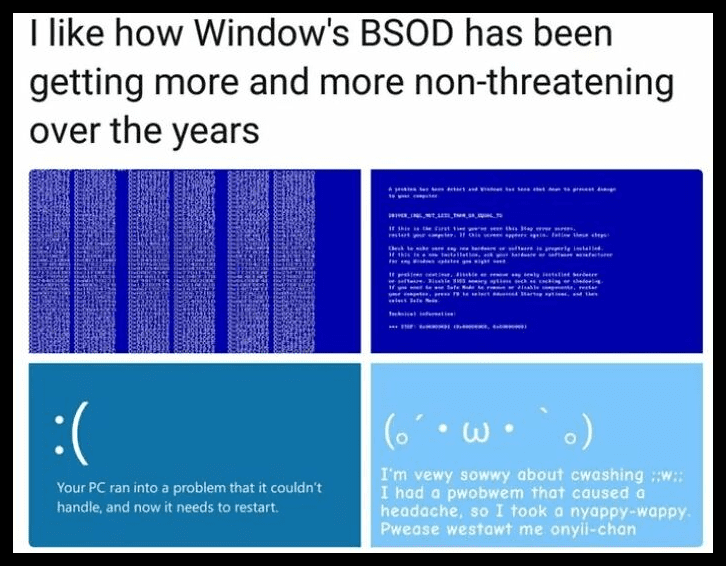
Over the years, it appears that Windows has become much tamer in the way it displays error messages. It started out as displaying sad emojis but has since completely changed into a cutesy language. We are honestly loving this transformation.
The Airport WiFi Situation
If you have long transit hours and have to sit around in an airport, you might get a bit bored. Thus, it would make sense that you would want to resort to the internet for some entertainment. Unfortunately, the airport WiFi does not always comply with the connection situation.

This could happen if the infrastructure is old or if there are too many people connected at the same time. To solve the problem, simply change your Mac address. Mac addresses are essentially unique identifiers for your physical device. No need to thank us for the free advice.
Power Of RAM
RAMs are temporary storage devices that are used to load a program that is currently running on the device. Storage devices used to be as small as 32 megabytes. It’s fascinating to see how far storage systems have come with technological advancements.

Nowadays, using an 8 gigabyte RAM is considered standard for mobile phones. An embedded 8 GB RAM can process an array of concurrent programs. However, it appears that a more powerful RAM is required for the PC. This meme of Morty explains the situation perfectly.
An Unpatched Server Issue
There is no other way to put it other than to say that you are a blithering idiot if you run an unpatched Exchange server that is accessible via the internet. Unpatched refers to a server that has not received all of Microsoft’s security updates in full.

If you have trouble understanding why servers need to be protected, just let Microsoft take care of the network security requirements. Servers shouldn’t be run by people who have no interest in installing security updates. It makes sense why this man is absolutely terrified of possibly catching sight of this many unpatched servers.
How Sad
When you log on to a computer running Windows 7 in a domain environment, it is common to receive the following error message. It must be a sad day if the device you’ve been working on for so long refuses to trust you.
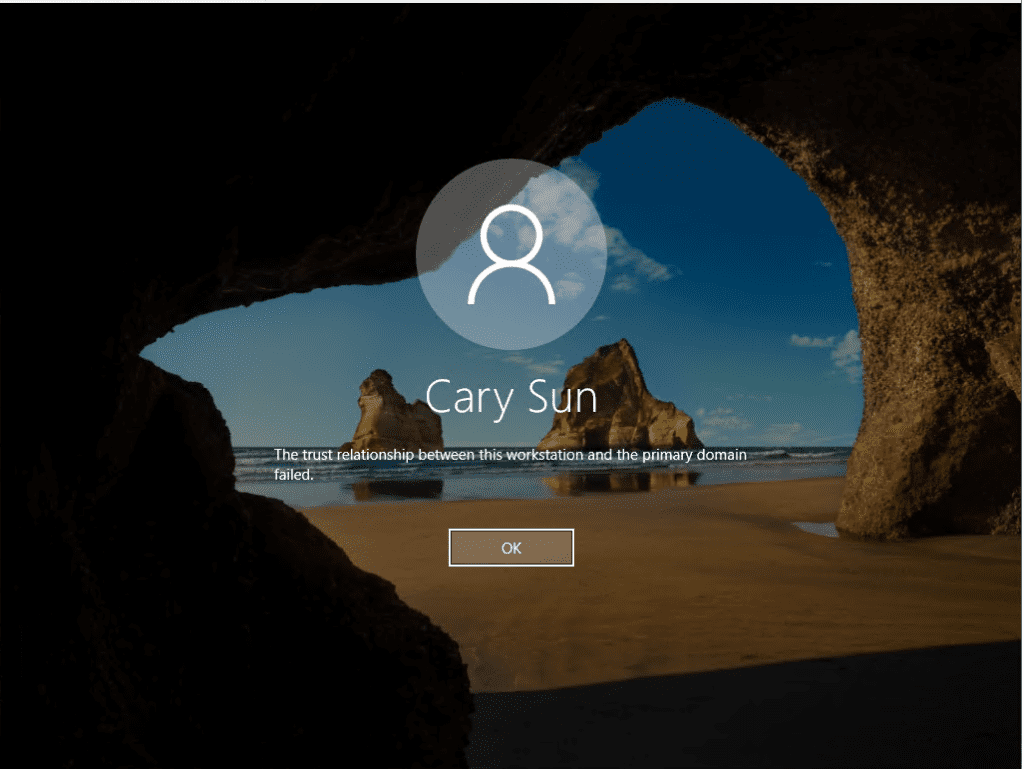
Microsoft, on the other hand, appears to elaborately list out the solutions to your problems and aid in the improvement of your trust relationship with the primary domain. Simply remove the domain from your computer and reconnect it to resolve this issue.
A Little Scary
There could be a variety of apocalypses that would be disastrous for the world. For example, consider a ghost invasion, a zombie apocalypse, or a nuclear war. Although these appear plausible, we are not immediately terrified by the thought of these atrocities.

However, there is one thing that can frighten even the most seasoned programmer. That is the use of characters in arrays. There are a handful of data type distinctions in the programming language. These range from integers, floating points, boolean to decimals. However, the use of character data type is the most dreaded by many.
We Demand An Explanation
In Linux, the Cat(concatenate) command is frequently used. It reads data from a file and outputs its contents. It assists us in the creation, viewing, and concatenation of files. This feature is handy when it comes to concatenating necessary resources.

There is, however, one lingering issue in this situation. If there is a command for cats, why isn’t there one for dogs? Why are these creatures not treated equally in society? Dogs are just as cute as cats but far more loyal. A demand for a dog command makes perfect sense to us.
Custom SQL Queries
SQL works by comprehending and analyzing data of any size, from small to large. It’s a very powerful tool that allows you to perform a variety of tasks with high efficiency and speed. Data retrieval has become much more efficient as a result of SQL.

If you’ve ever worked with SQL queries, you’ll know that the majority of declarative sentences require the use of capital letters. As a result, it would make sense to capitalize the queries more frequently using the Caps lock feature. It can also be quite fun to create custom queries.
Contradictory
If we put it simply, the cloud is the internet. It is basically everything you can access remotely via the internet. When something is in the cloud, it is stored on Internet servers rather than your computer’s hard drive. As a result, this technology is quite robust.

As we can see, one poster implies that the cloud is moving, whereas the other claims that the cloud is approaching us. We’re not sure which statement to believe because they’re both contradictory. We shouldn’t be concerned as long as the cloud can efficiently back up our data.
Two Types Of Programmers
Although programming requires many mathematical approaches, we believe that it can also be considered a form of art. The perfect indentation and placement of your codes can genuinely determine how clean your code is. This divides programmers into two types.
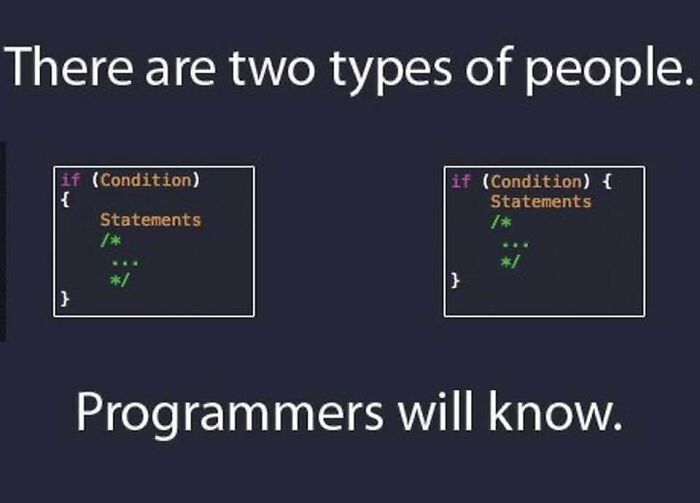
As we can see, some programmers like to add a line after declaring the IF condition to put the curly braces. Others, on the other hand, prefer to place the braces immediately after the IF condition declaration. Thus, arises the distinction of coding patterns. The first approach, in our opinion, is cleaner.
The Dilemma
Deployment architectures can vary greatly, but in general, the tiers begin with development (DEV) and end with production (PROD). Most people appear to make the silly mistake of copying data from DEV to PROD rather than the other way around.

If you don’t have a database backup in PROD, this can lead to a bigger problem. This means that your information will be lost. Data has tremendous value. People working in IT certainly know the writhing agony of losing valuable data.
Some HTML Humor
Although HTML (Hypertext Markup Language) is not strictly a programming language, it is an essential tool for creating the structure of web pages. HTML, like any other technology, has gone through several iterations over the years. Currently, HTML 5 is being applied by most users.
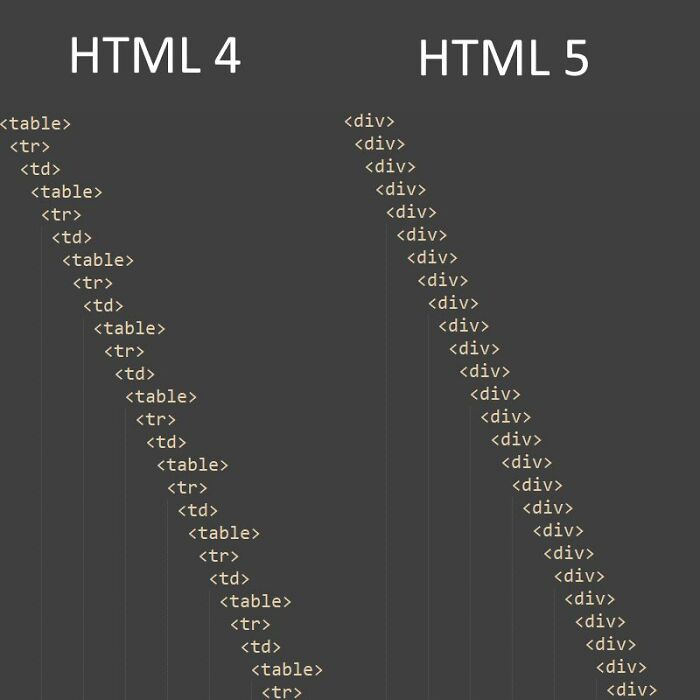
When compared to its predecessor, however, there are significant differences in content placement. HTML 4 made extensive use of the table and tr tags to separate content. The latest version, on the other hand, has come a long way by specifying only the div tag for the same purpose.
The Anti-malware Issue
Our computers are no strangers to malware. As a result, the Antimalware Service Executable process is included in Windows Defender. It is a built-in antivirus program included in Windows. It performs real-time scanning and is in charge of scanning files for malware whenever you access them.

The scanning capability of this software is heavily reliant on your computer’s CPU. That is why Antimalware Service Executable consumes a lot of CPU, disk space, memory, RAM, and even network bandwidth. As a result, this SpongeBob meme perfectly depicts how an anti-malware program drains the system’s HDD and RAM.
PC On Steroids
If you understand how nature works, you will realize that nothing is perfect. However, this PC’s performance statistics appear to suggest otherwise. This PC is the equivalent of the over-achieving kid in middle school—but better. We don’t know if this PC was confiscated in any way.
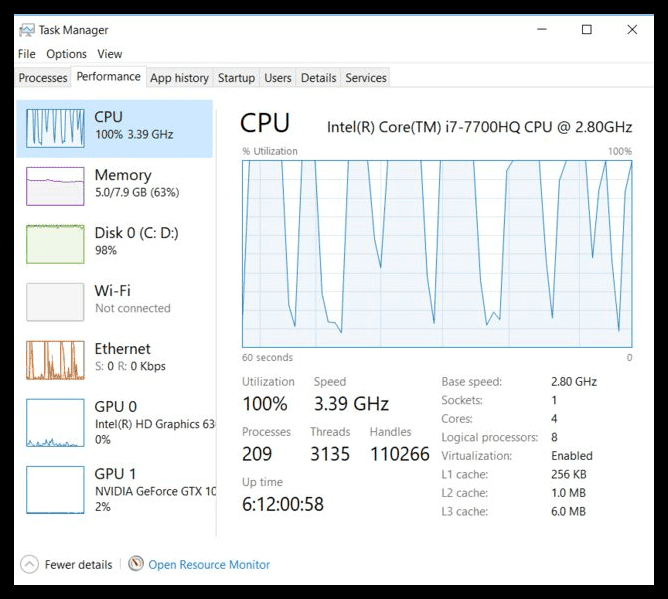
As we can see, the utilization rate of this PC is 100%. It could undoubtedly compete with the speed of light at that rate. Although we’re not sure what happened to this PC to make it so fast, programmers undoubtedly require a powerful PC like this to streamline their work.
The Three Musketeers of IT
You might believe that the only thing necessary to deploy an application is to build it from the ground up. You might be surprised to learn that we need more than just programmers to run an application. Server administrators and network administrators are also needed.

Therefore, these three stakeholders are always involved whenever something goes wrong with an application. This scene from Harry Potter sums up what happens when an application malfunctions. It is always these three unfortunate souls that are called for immediate answers.
